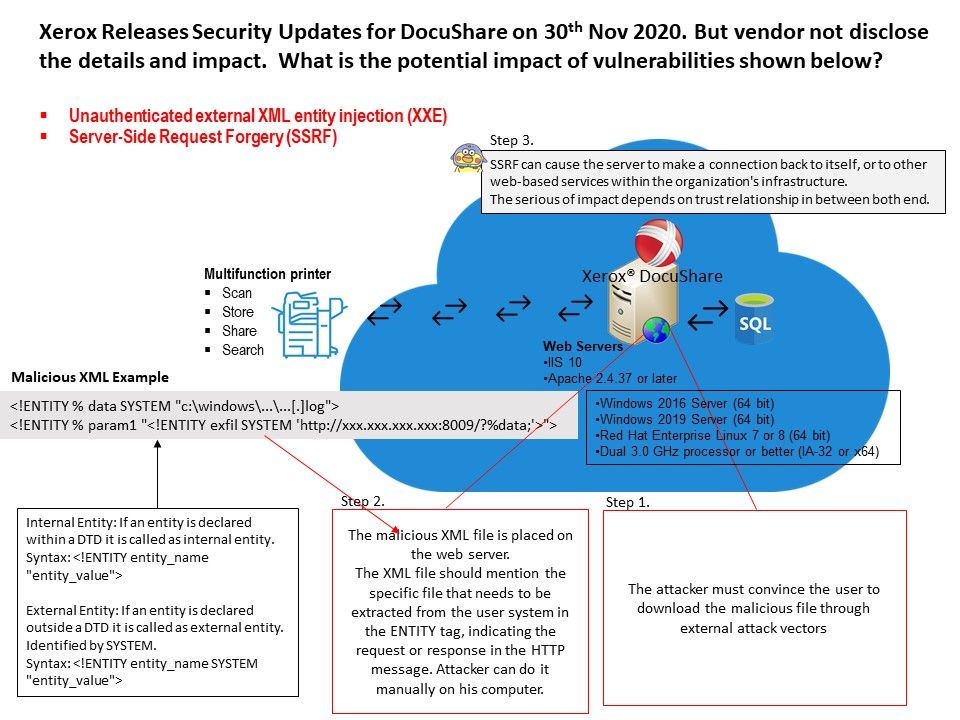
Sequoia: A Local Privilege Escalation Vulnerability in Linux's Filesystem Layer (CVE-2021-33909) | Qualys Security Blog
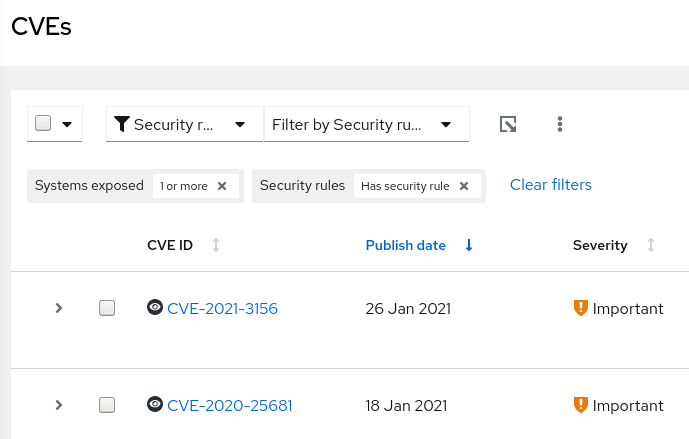
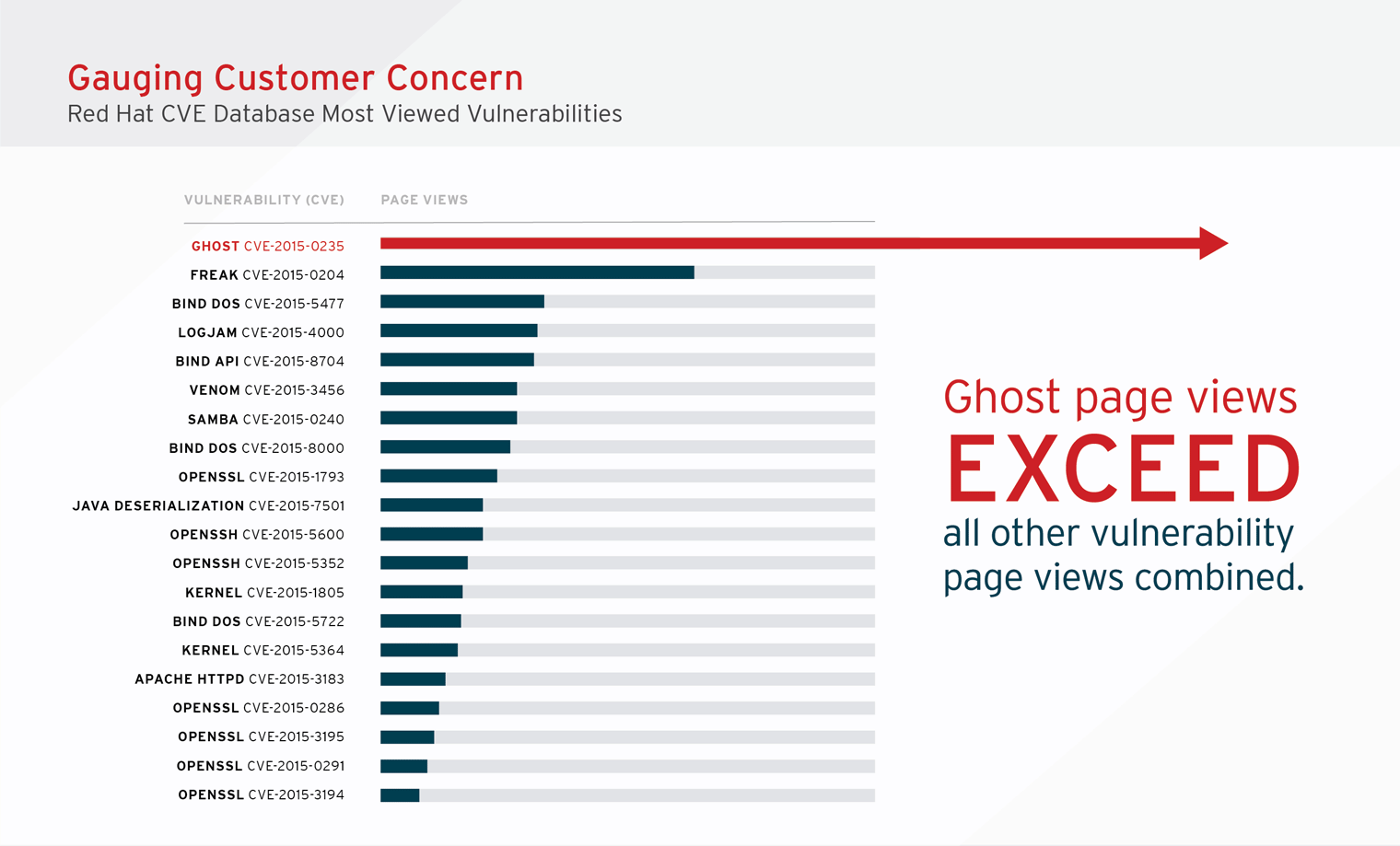
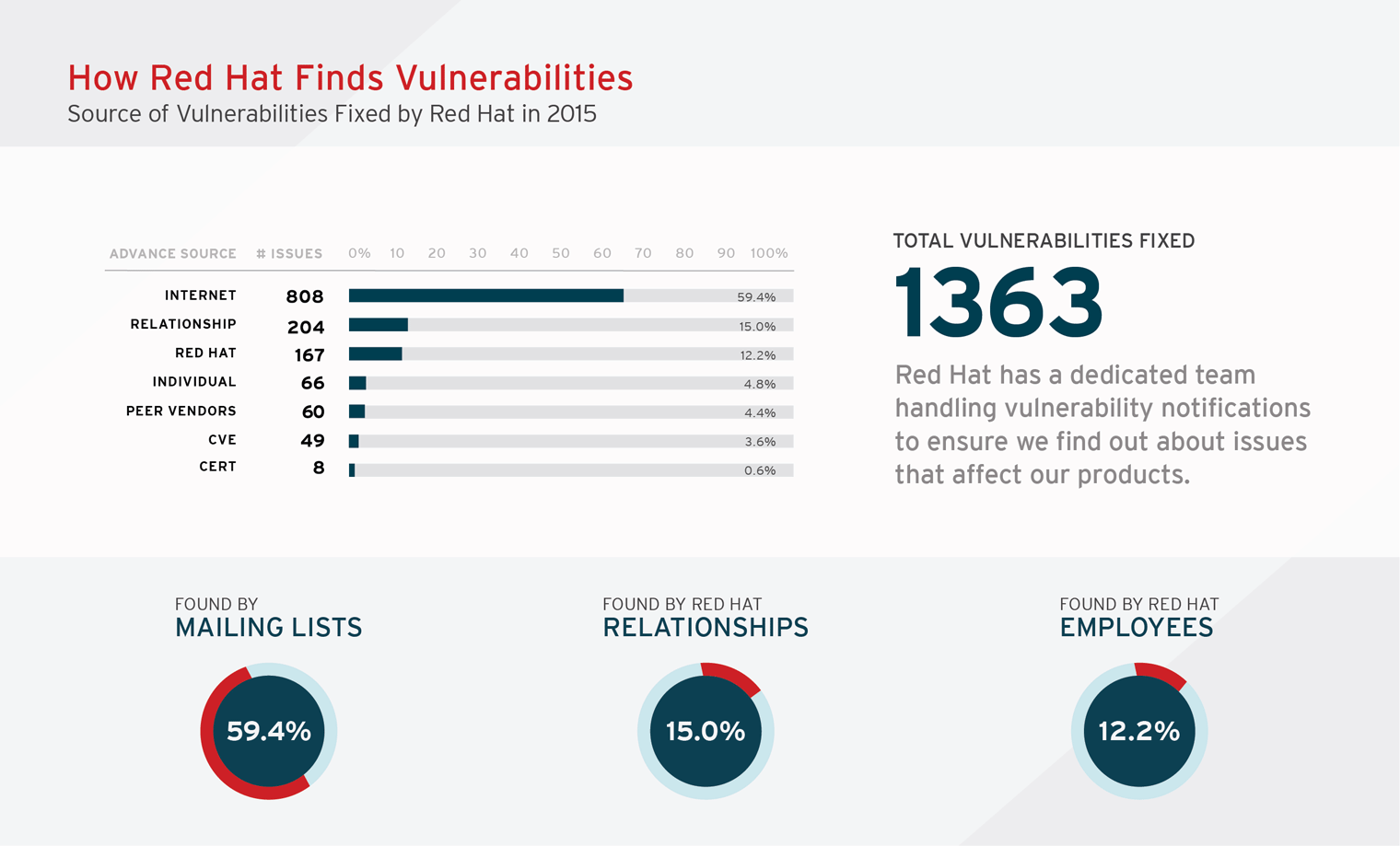
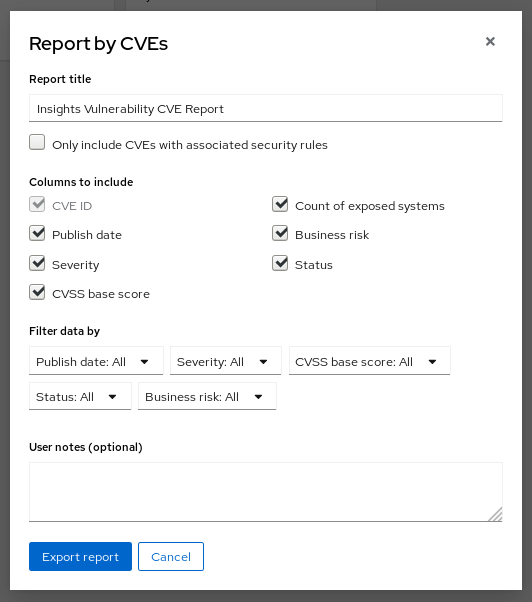
Assessing and Monitoring Security Vulnerabilities on RHEL Systems Red Hat Insights 2020-10 | Red Hat Customer Portal
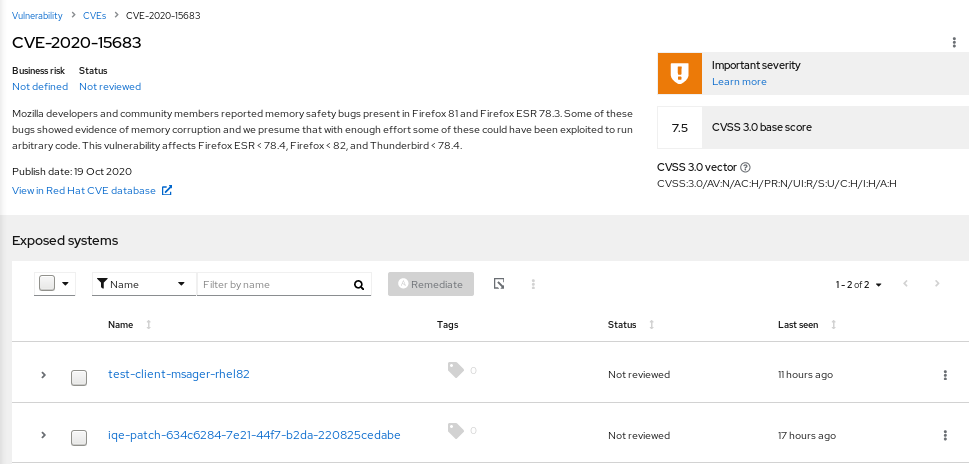
Assessing and Monitoring Security Vulnerabilities on RHEL Systems Red Hat Insights 2020-10 | Red Hat Customer Portal

Sequoia: A Local Privilege Escalation Vulnerability in Linux's Filesystem Layer (CVE-2021-33909) | Qualys Security Blog
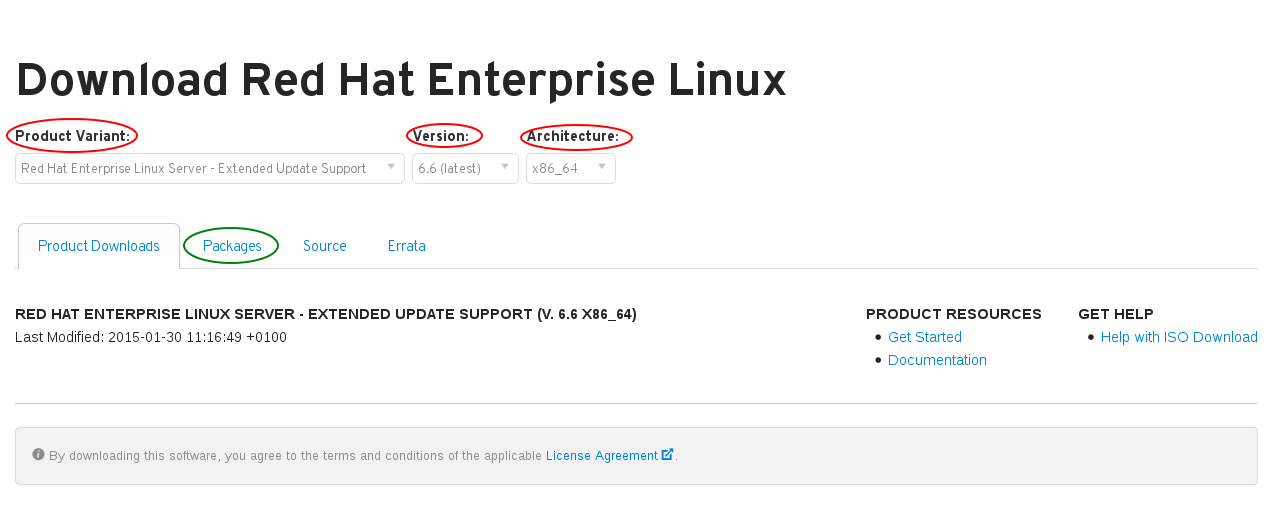
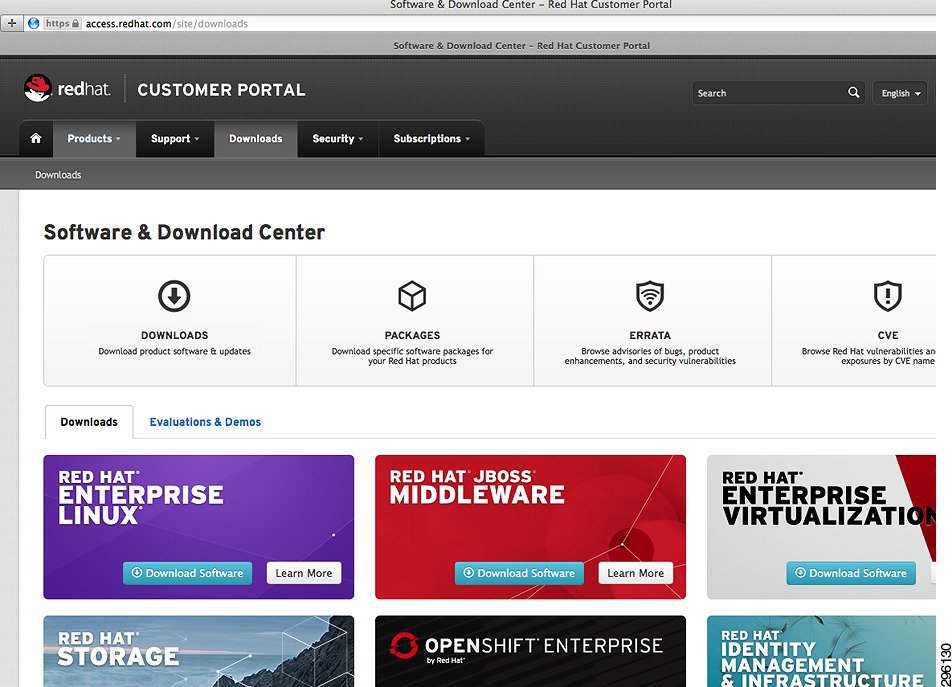
How do I download a package from the "access.redhat.com" Customer Portal site? - Red Hat Customer Portal

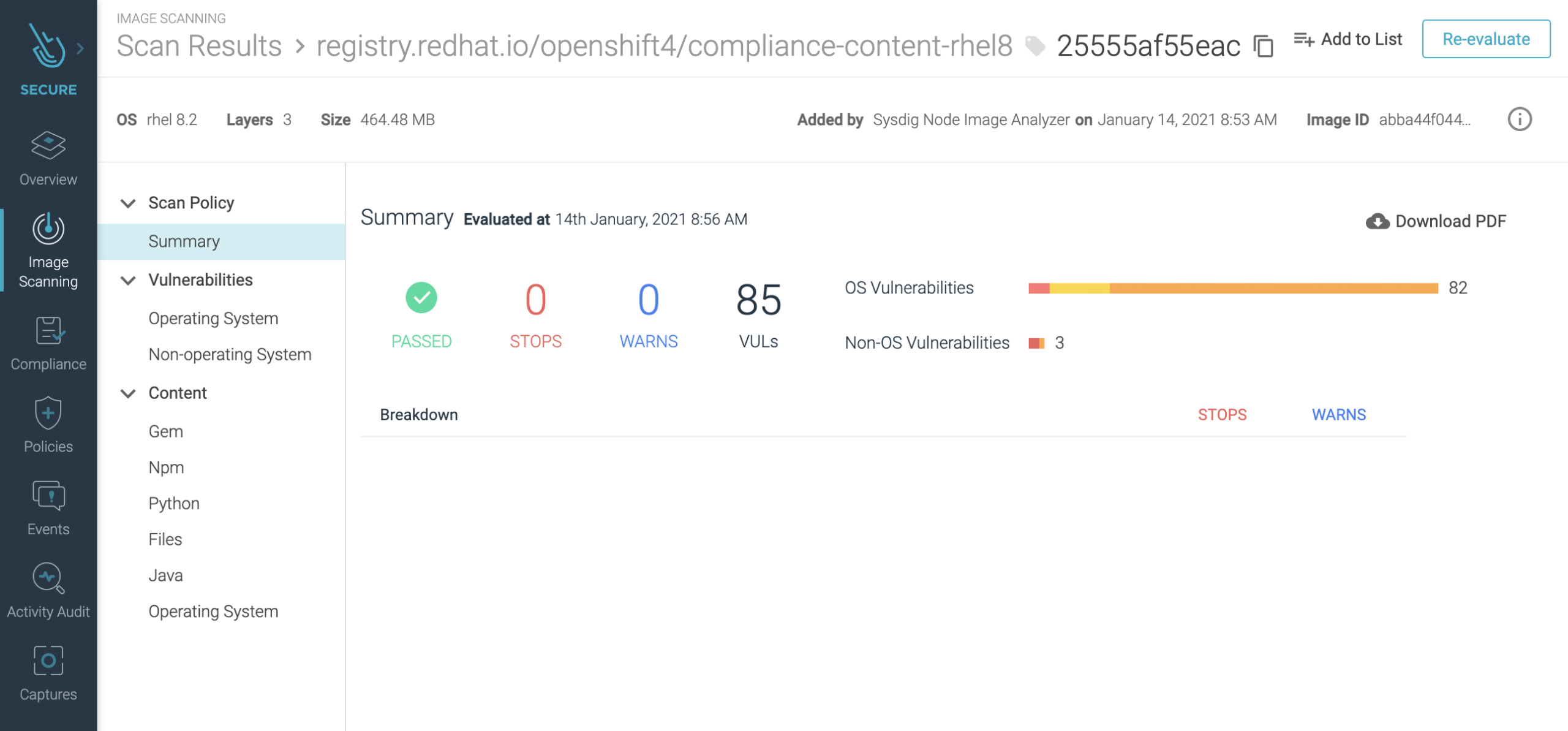
How To Fix CVE-2021-43267- A Heap Overflow Vulnerability In Linux Kernel's TIPC Module - The Sec Master
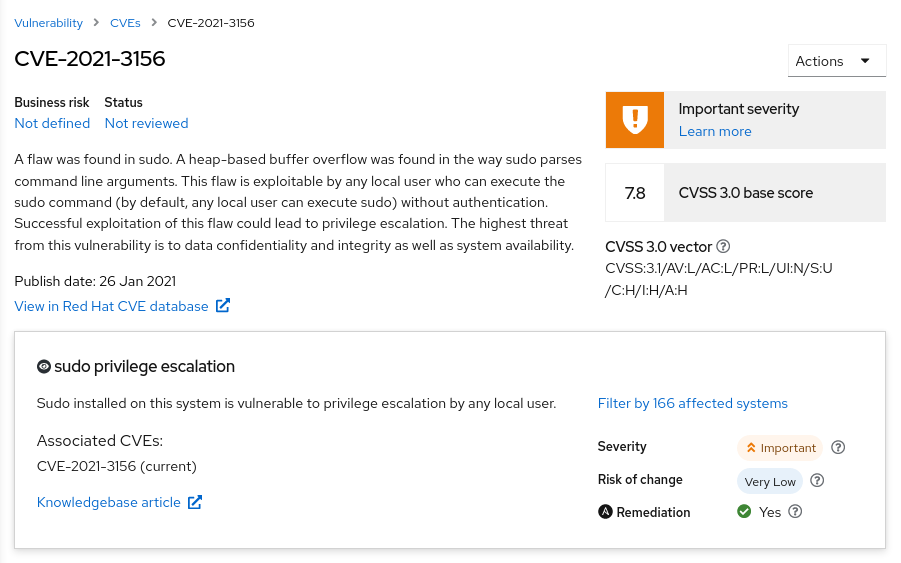
Assessing and Monitoring Security Vulnerabilities on RHEL Systems Red Hat Insights 2020-10 | Red Hat Customer Portal