Hands-On Web Penetration Testing with Metasploit : The subtle art of using Metasploit 5.0 for web application exploitation (Paperback) - Walmart.com
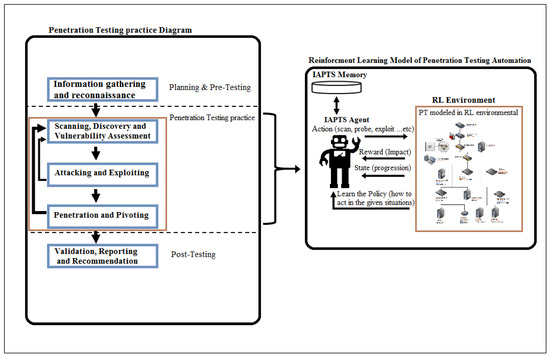
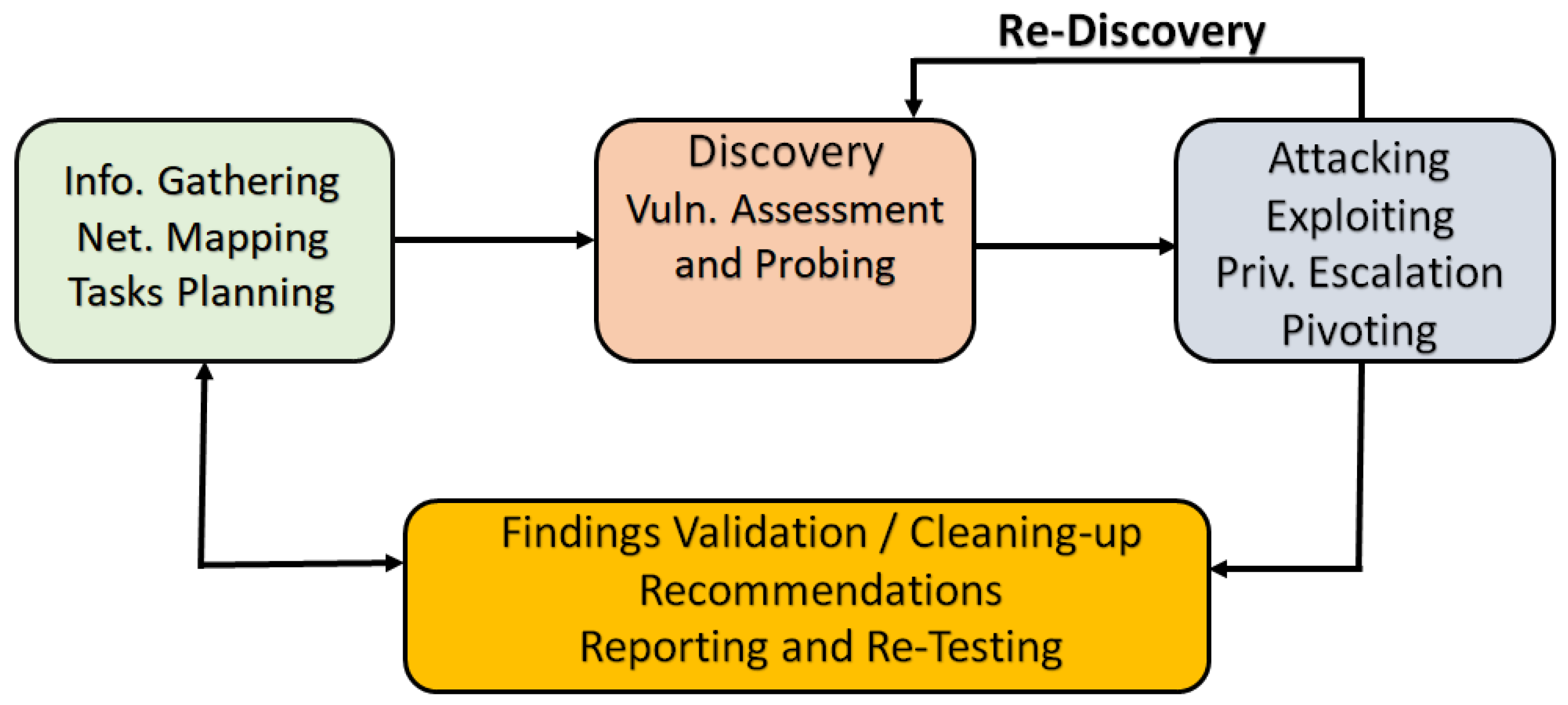
Information | Free Full-Text | Reinforcement Learning for Efficient Network Penetration Testing | HTML





:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/21785592/us_army_srr_candidate_comparison_draft.jpg)
/cdn.vox-cdn.com/uploads/chorus_image/image/67231539/hadron_cscphoto_07851jpg.0.jpg)